How to Check the Sender's Email Address
The first thing you should always do when opening an email is to check the sender's email address. Email verification is your first line of defense against scammers. If the email is from a company you've never done business with, or from a person you don't know, treat it with caution.
You may also receive emails that look like they come from someone you know, but upon closer inspection, are fake email addresses. Check for common red flags such as typos, misspellings, and strange domain names.
The domain name is the part of the email address that comes after the "@" symbol. If it isn't one you recognize, or it has a lot of strange numbers, letters, and characters in it, do not trust the sender.

You can even use an email verification tool to check if an email address exists. Free online tools such as AbstractAPI's Free Email Verification API allow you to check if an email account is valid.
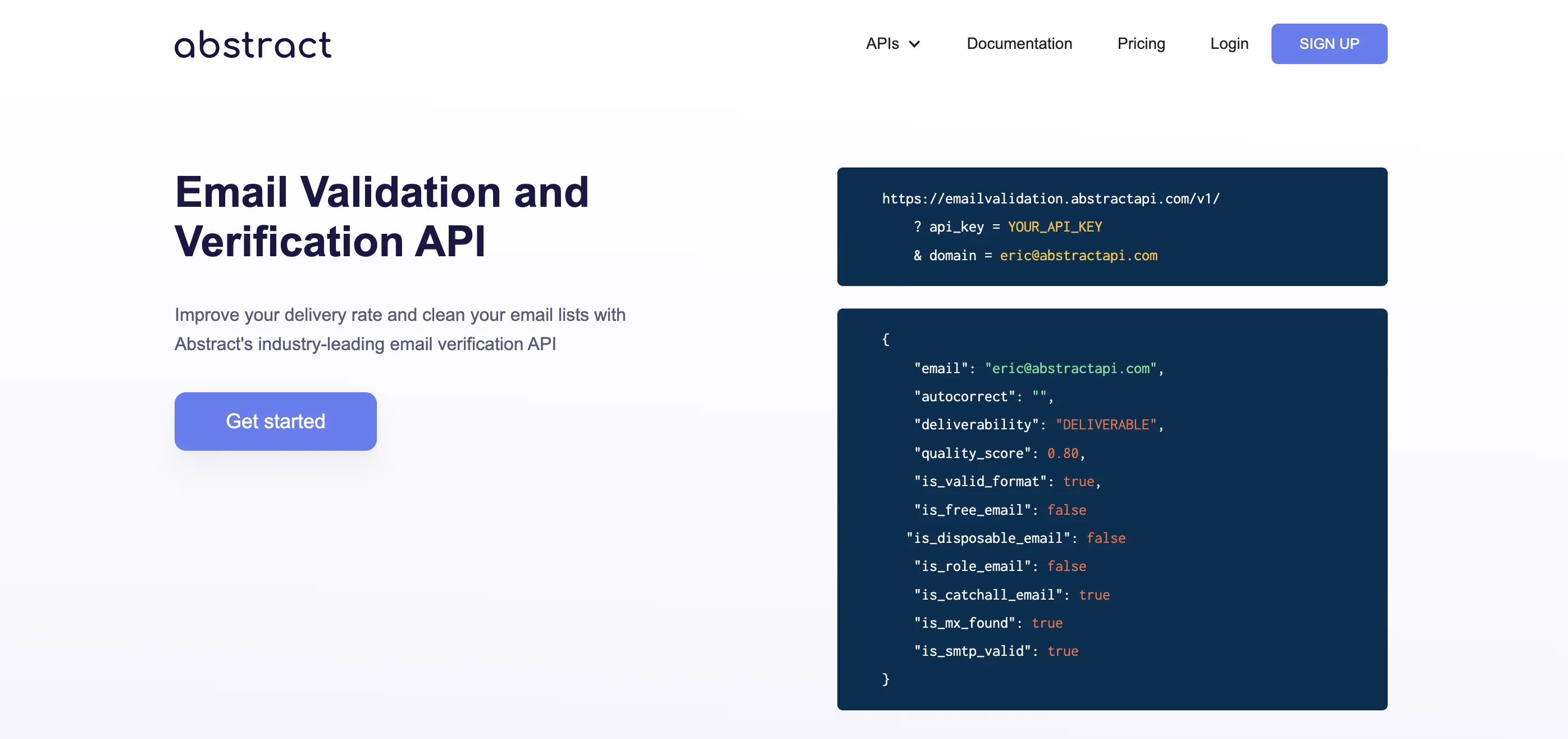
To do email verification using the free email verification API, simply click the blue "Get Started" button, then copy and paste the email address into the "Live Test" box, after the "email=" and click "Make Test Request."

How to Check the Email's Content
Once you've used email verification to check the sender's email address, you should also check the content of the email for suspicious items. Often, a phishing email might include a message that looks as though it came from a family member, and a link to look at some photos, a video, or something else.
Read the content carefully and look for typos, the tone and language of the message, the email signature and footer, and any suspicious requests or links. If the email message is from a domain you do not recognize do not click ANY links!
How to Check the Email's Attachments
Treat attachments to any email very carefully. If the domain name of the email address is suspicious, don't open any attachments. If the wording in the email sounds "off" or weird in any way, don't open any attachments.

Always verify the sender and content of any email before opening an attachment. You can also use antivirus software to scan attachments. Many email clients provide scanners for you (Gmail, for example, will warn you if an attachment seems suspicious.)
How to Check for Email Phishing
Email phishing is an attempt to make you believe that an email comes from a trusted source - either a reputable organization or a known friend or family member. The email will encourage you to divulge personal information, such as account credentials, ID numbers, home addresses, phone numbers, etc.
A typical phishing scam might look like it comes from a reputable company like PayPal, and the email message might say that some type of action is needed urgently on your account. You are provided a link, which will take you to a fake login page where you can input your PayPal account information.
The email scammers now have access to your PayPal account, and potentially even more than that.
The best way to avoid falling for a phishing scam is to check the domain name of the email address, and never use a link found in an email to log on to a company website. Always retype the URL for the company site into your browser instead.
How to Check for Email Spoofing
Email spoofing is similar to phishing, however, the difference is that in a spoofing attack, the actual email address of the sender has been compromised. Rather than using a fake email that looks very similar to a legitimate email address, the spoofers have gained control of a real email address and are using it to attack people.

This means that even if you verify that the email address is valid, the content of the email could still be attempting to gather personal information from you. The best thing to do if you receive a link or suspicious request from a friend or family member is to reach out to them independently (don't reply to the email) and ask if they sent it.
If the message comes from an organization and asks you to click a link to log in to your account, go to the company website via your browser instead and log in that way.
How to Check for Email Domain Spoofing
Email domain spoofing is a form of phishing email scam where the attacker impersonates a known business or person using a fake website or email domain. Once the recipient believes that the attacker is legitimate, they will be asked to disclose personal information or log on to a fake website.
Again, always verify email addresses before disclosing personal information. Check the web address of any website you are asked to log on to make sure it is a legitimate website for the actual company.
How to Check for Email Scams
There are many different types of email scams. Some entail a person using email to build a rapport with you and gain your trust through a series of communications before attempting to take advantage of you and get money or personal information.

Others might come in the form of free gift offers, fake tech support emails, or the classic "Nigerian Prince" scam. Here's a non-exhaustive list of the types of email scams to be aware of, and the best way to avoid them:
- tech support scams - you get a message from a company saying they noticed a problem and need you to log in to your account. To avoid: real companies don't usually reach out like this out of the blue
- online dating scams "aka Catfishing" - you meet someone online and things progress quickly. At a certain point, they ask for personal information or tell you there is an emergency and need you to send money. To avoid: never send money to someone you meet online without meeting in person.
- emergency scams "aka Grandparent Scams" - a form of a phishing email or spoofing in which a relative says they are in urgent need of money. These can also happen over the phone. To avoid this: call the person back at the number you have saved for them to verify that they really need help.
- free gift scams - be wary of any out-of-the-blue email message that offers a free gift. Sometimes you will be required to complete surveys or other offers to qualify, and you may end up disclosing personal information in the process. To avoid: be wary of any "free" gifts
- advance fee scams - a scammer offers a payment, loan, grant, or prize, but first you must invest some money upfront. To avoid: ask yourself why you need to pay upfront in order to receive the loan or prize.
- malware scams - you receive an email with a sensational headline or clickbait-y subject containing a link to an amazing video or image. To avoid: be wary of any links sent in emails. Verify the sender's address before you open it.
- foreign money exchange scams "aka the Nigerian Prince" - a "foreign dignitary" (or their spouse) or some "government official" wants to deposit money into your account. The catch is, first you must pay their "taxes" or "transaction fees." To avoid: never send money in order to collect money.
How to Check for Business Email Compromise
Business email compromise (BEC) is a type of email scam that targets and attempts to defraud a company. There are 5 types of business email compromise:
- CEO Fraud: Scammers pose as the CEO or other high-ranking company official and email someone in the company (typically in the finance department) asking that funds be transferred to an account controlled by the scammer.
- Account Compromise: Scammers hack an employee account and use it to request payment from vendors. Payments are sent to fraudulent bank accounts owned by the scammers.
- False Invoice Scheme: Scammers pose as foreign suppliers and request payment from the company through fake invoices.
- Attorney Impersonation: Scammers pose as lawyers or legal representatives and target low-level employees, asking for sensitive information.
- Data Theft: Scammers target HR representatives and attempt to obtain personal or sensitive information about company individuals such as CEOs. This data can then be used in future attacks such as CEO Fraud.
If you are an employee and receive a request from a vendor, lawyer, or executive within the company, always verify the validity of the request, either with the individual themselves or with another person at the company.

How to Check for Email Hacking
Email hacking happens to many people. Once a person's email address has been hacked, it can be used to send spoofed emails to other people. This is why it's always important to verify with the sender that they did indeed send the email before you click any links or open any attachments.
To prevent your own email from being hacked, the first thing you should do is create strong, unique passwords for all your online accounts. Email addresses are typically accessed when other online accounts are hacked and user data is leaked.

Next, consider setting up 2-Factor Authentication (2FA or MFA) to protect your email account. This adds a login step that requires you to obtain a code via text message or through an authenticator app.
Finally, use the tips outlined in this article to avoid falling for email scams and disclosing personal information to hackers through your email. use email verification to validate email addresses and check if an email is legitimate.
Email Graymail
Graymail is not a dangerous thing - in fact, graymail emails are perfectly legitimate emails. Graymail is an email that is sent in bulk to many recipients, and that has varying value to the recipients. For example, a monthly email newsletter or periodic updates, announcements, or ads for a company could be considered graymail.
If you've previously signed up for correspondence with a company (maybe you gave them your email address in exchange for a free download) you might receive these types of emails. If you don't want to receive them anymore, simply unsubscribe or filter them into spam.

Email Privacy Violations
Make sure that the graymail you receive doesn't violate any privacy laws. Companies that send bulk emails such as newsletters and ads should abide by privacy laws. Every email should include an easily visible unsubscribe link, and the company website should have a privacy policy made readily available.
If the emails you're receiving do not include an easy way to unsubscribe, you should report the email as spam using your email client.
How to Use Email Filters and Rules
One of the best ways to protect your inbox is to set up email filters and rules. Most email clients make this very easy. Most filter out spam automatically (in fact, you may miss some emails from legitimate companies because they end up in your spam folder by mistake.)
You can also customize filters, label emails, and control which emails end up in your inbox. Let's take a look at how to set up an email rule in Gmail to protect yourself against spam and fraudulent emails.

How to Set Up a Filter in Gmail
- Open Gmail.
- In the search box at the top, click Show search options.
- Enter your search criteria to find the emails you want the filter to apply to. To check that the criteria are correct, click Search to see what emails show up.
- At the bottom of the window, click Create filter.
- Choose what the filter should do.
- Click Create filter.
How to Use An Existing Email to Create a Filter
- Open Gmail.
- Check the checkbox next to the email you want.
- Click More.
- Click Filter messages like these.
- Enter your filter criteria.
- Click Create filter.
How to Report Fake Emails
The easiest and most effective way to report a fake email is to send the addresses of phishing emails you receive to the following email address:
This is an email used by the Anti-Phishing Working Group, which includes ISPs, security vendors, financial institutions, and law enforcement agencies. They will make a note of the email and follow up with the prosecution.

If you receive a spoofed email from the account of someone you know, let them know immediately that you think their account may have been hacked. You should also reach out to other friends and family members and tell them not to open any emails from that person.
Conclusion
Scams that use mail servers are rampant in this day and age. It can feel overwhelming to think about having to defend against them. The good news is, if you use an email server like Gmail or Outlook, much of this defense will be done for you. They are excellent at preventing fraud and keeping your inbox safe.
However, you should always treat email attachments and links within emails with caution. Always verify the address of the sender before opening any email - you can even use email verification services to do this.
Once you open an email, check the content for red flags and known scams. Never use a link from an email to log on to a company site, and never send someone money based solely on an email request.
It takes a little diligence to stay ahead of hackers and scammers, but it is an important task to keep yourself and your loved ones safe.
FAQs
What are some common signs of a fake email?
Typos, odd-looking domain names that include numbers or misspellings, links that ask you to log on to a company website or provide other credentials, language, or a tone that you don't recognize from a known individual like a family member. Requests for money, free gifts, and tech support from out of the blue.
Can scammers spoof the email address of a legitimate business?
Yes. Scammers can absolutely gain access to email accounts from a legitimate businesses (they sometimes do this by targeting HR representatives within the company to get personal information about employees.) Never click a link to a company website within an email. Always type the website address into your browser and log on that way.
What should I do if I accidentally opened a suspicious email?
Opening suspicious emails is not the end of the world as long as you haven't clicked any links or opened any attachments. The best thing to do if you realize an email is suspicious is to report it to the Anti-Phishing Working Group (reportphishing@apwg.org.)
If you have clicked a link or opened an attachment, immediately disconnect your device from the internet. Back up all your files. Scan your computer for malware. Change your credentials on any sites that contain sensitive data. Set up a fraud alert. Contact your financial institution. Report the email address.
How can I report a fake email if I don't know who the sender is?
The best thing to do if you realize an email is suspicious is to report it to the Anti-Phishing Working Group (reportphishing@apwg.org.) Send them an email explaining what you received and the email address that it came from.




